When authentication fails, users don’t complain, they leave.
That was the challenge facing a large professional association in the architecture and planning industry, operating multiple member-facing digital products. Their Universal Login experience had become unreliable, hard to evolve, and increasingly risky from a security standpoint. What started as “occasional login issues” was actually a deeper architectural problem.
At Streaver, we were brought in not just to fix bugs, but to rethink how identity should work at scale.
The client’s existing SSO system was built on AWS Cognito, but over time it had accumulated complexity in all the wrong places.
The most critical issue was a race condition during sign-up:
On top of that, error handling was fragile. When something failed, recovery was unclear, both for the system and for the user.
There were also security and scalability concerns:
This wasn’t just a technical inconvenience. It directly impacted user trust, internal velocity, and the ability to safely evolve the platform.
Our objective wasn’t to add features, it was to remove uncertainty.
We aligned on a few clear goals:
In short: make authentication reliable, scalable, and invisible.
Instead of extending yet another custom authentication layer, we leaned into what AWS already does well.
We rebuilt the platform using AWS Cognito’s managed login experience, combined with a clean, event-driven backend that gives us explicit control over when and how side effects occur. The result is a simpler, more reliable SSO architecture that’s easier to reason about, operate, and evolve.
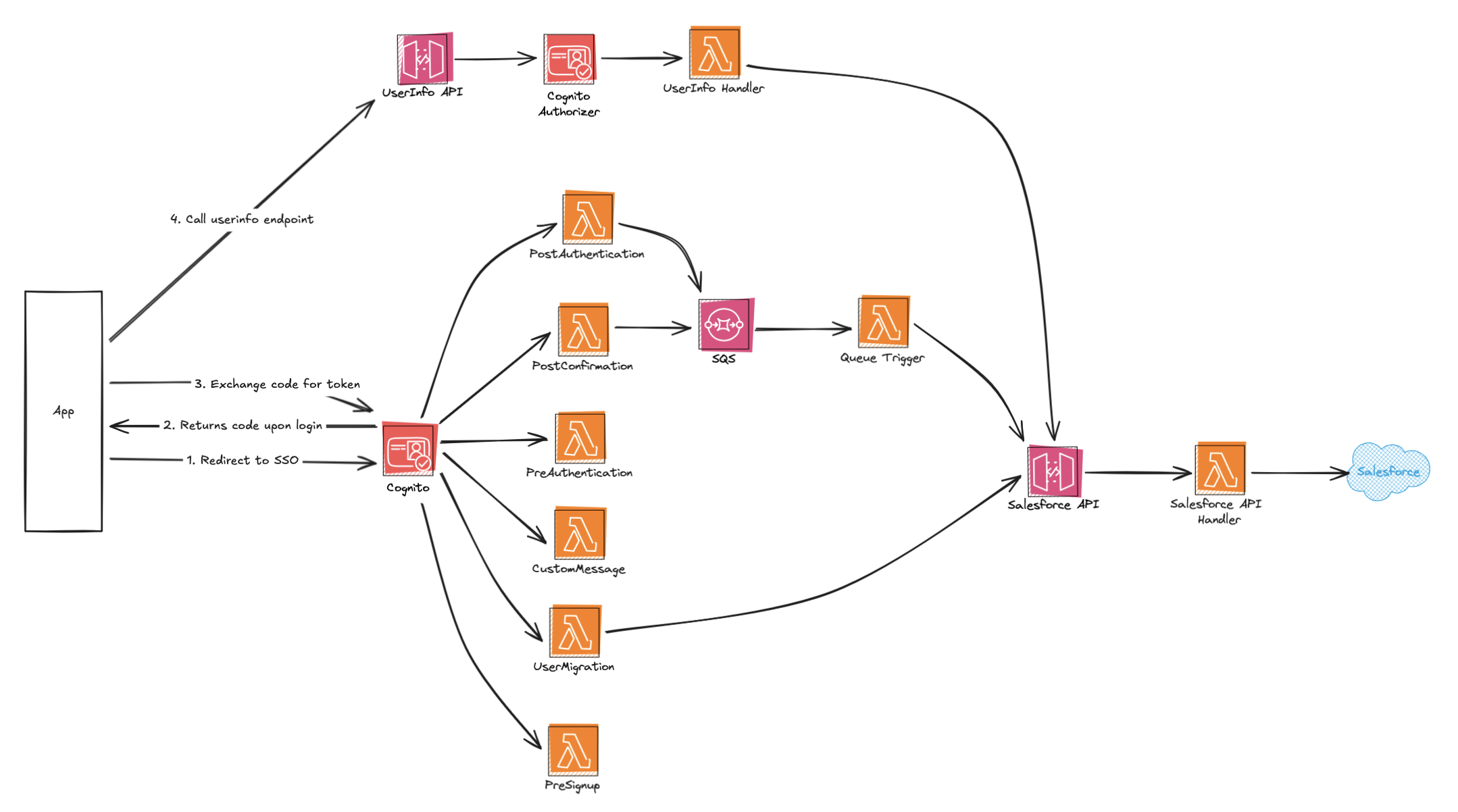
At the core of the new system is AWS Cognito’s Managed Login, paired with Cognito’s standard OAuth 2.0 endpoints for authorization, token issuance, and logout.
Rather than implementing custom OAuth logic, we relied on Cognito’s compliant /authorize, /token, and /logout endpoints while using the Managed Login solely for the user-facing authentication experience. This allowed us to keep full control over application flows without taking on the risk of maintaining a bespoke OAuth server.
Authentication, token lifecycle management, and standards compliance are now handled by Cognito, while the rest of the platform focuses on business logic and system integration.
This separation reduced security risk, simplified long-term maintenance, and made it straightforward to introduce additional capabilities such as MFA in later phases.
The most critical fix addressed the race condition between user authentication and CRM user creation.
AWS Cognito triggers have a strict execution time limit, which makes them unsuitable for long-running or failure-prone integrations such as creating users in an external CRM. Attempting to perform these operations synchronously during sign-up had previously led to timeouts, retries, and inconsistent user states.
To solve this, we introduced a deterministic, event-driven flow:
By moving CRM integration out of the authentication path, we respected Cognito’s execution constraints while gaining explicit control over ordering, retries, and failure handling. This eliminated partial user states and made the sign-up process predictable, resilient, and easier to operate.
/userinfo API for Salesforce DataTo avoid coupling internal applications directly to Salesforce, we introduced a custom /userinfo API.
Built as a serverless REST endpoint using API Gateway and Lambda, this service:
contact_id from Cognito user attributesThis approach keeps authentication fast while allowing applications to retrieve enriched user data through a single, stable interface.
Reliability requires visibility.
We introduced structured logging, CloudWatch dashboards, and alarms to provide real-time insight into authentication flows and failures. Issues that were previously hard to diagnose are now immediately observable and actionable.
At the same time, we implemented a fully automated CI/CD pipeline using GitHub Actions, Terraform, and AWS SAM. Infrastructure and application code are deployed consistently across environments with zero manual steps. Deeper observability with Datadog was planned for Phase 2.
One of the most delicate parts of this project was migrating more than 150,000 existing users from a legacy User Pool to a new one. A traditional migration would have required forcing password resets or scheduling a coordinated cutover, both of which would have introduced friction and risk.
Instead, we relied on Cognito's UserMigration trigger to make the transition effectively invisible.
When a user attempts to sign in and does not yet exist in the new User Pool, Cognito automatically invokes the migration trigger. At that point, our system retrieves the required user data from Salesforce, which remains the source of truth, and creates the user in the new pool on the fly.
From the user's perspective, nothing changes.
They log in exactly as they always have, using the same credentials, without being prompted to reset passwords or take any additional steps. Behind the scenes, the account is migrated, attributes are synchronized, and the user is now part of the new identity platform.
This approach allowed us to migrate users progressively and safely, only when they actually signed in, instead of attempting a risky bulk migration.
Most importantly, it preserved trust. Users never had to think about the migration at all — which is exactly how authentication systems should behave.
By leaning on managed services and event-driven design, we reduced complexity rather than adding to it. Authentication is now reliable, scalable, and easy to extend — exactly what a modern identity platform should be.
This project wasn’t just about AWS services. It worked because of how decisions were made.
Instead of adding complexity to “fix” complexity, we removed it.
The impact was immediate and measurable:
Just as important, the platform is now ready for what’s next; including MFA and future identity integrations without another rewrite.
Authentication is not where you want creativity. It’s where you want clarity.
By relying on managed services and clean event flows, we helped this organization turn a fragile SSO into a foundation they can trust.
This is the kind of work Streaver focuses on:
No unnecessary layers.
No over-engineering.
Just systems that do what they’re supposed to do, reliably.
Let’s talk about how Streaver can help you build systems that scale, stay secure, and get out of your users’ way.
👉 Explore what we do !





